information security policy template WombatSecurityAdTechnology is not enough when it comes to security best practices Get Security Awareness Results information security policy template kensaq Information Security Policy Template NowAdSearch for Information Security Policy Template on the New KensaQ
resources policiesA policy is typically a document that outlines specific requirements or rules that must be met In the information network security realm policies are usually point specific covering a single area For example an Acceptable Use policy would cover the rules and regulations for appropriate use of the computing facilities information security policy template security policy See an information security policy template and learn how to write one using the ISO 27001 standard as a sample information security policy See an information security policy template and learn how to write one using the ISO 27001 standard as a sample information security policy csoonline SecurityPhysical security Clean desk policy The clean desk policy of a company with approximately 2 000 employees that offers human resource and administrative services to companies looking to outsources those functions Read more Cell phone use while driving policy This sample cell phone usage policy pertains to employees who are on
pronto Information Security Policy Template NowAdFind Information Security Policy Template Compare Results information security policy template csoonline SecurityPhysical security Clean desk policy The clean desk policy of a company with approximately 2 000 employees that offers human resource and administrative services to companies looking to outsources those functions Read more Cell phone use while driving policy This sample cell phone usage policy pertains to employees who are on policyA Security policy template enables safeguarding information belonging to the organization by forming security policies In any organization a variety of security issues can arise which may be due to improper information sharing data transfer damage to the property or assets breaching of network security etc
information security policy template Gallery

it policies1, image source: chrisdill.wordpress.com
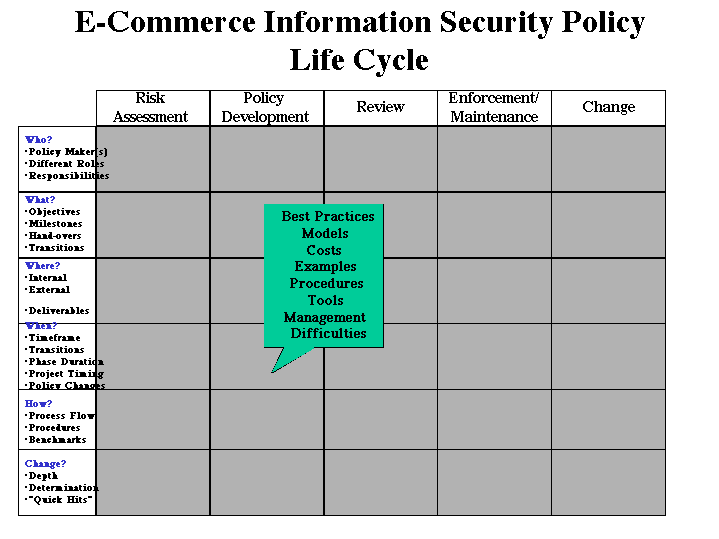
slide3, image source: www.cerias.purdue.edu

fig2 7, image source: www.globalsecurity.org

iso 27001 isms statement of applicability 4 638, image source: www.slideshare.net
![]()
bycourses bb, image source: www.greenskeeper.org

img034, image source: www.globalsecurity.org

air force policy letter example_245221, image source: namanasa.com

Data_Explorer, image source: www.metricstream.com

416962, image source: www.cisco.com

022713_1507_ExceptionMa1, image source: resources.infosecinstitute.com

professional business card template, image source: www.arenareviews.com

sorority recommendation letter sample famous see example, image source: marevinho.com

project status report final quintessence template excel example 620x366, image source: marevinho.com

standard arizona residential lease agreement 600x794, image source: rentallease.net
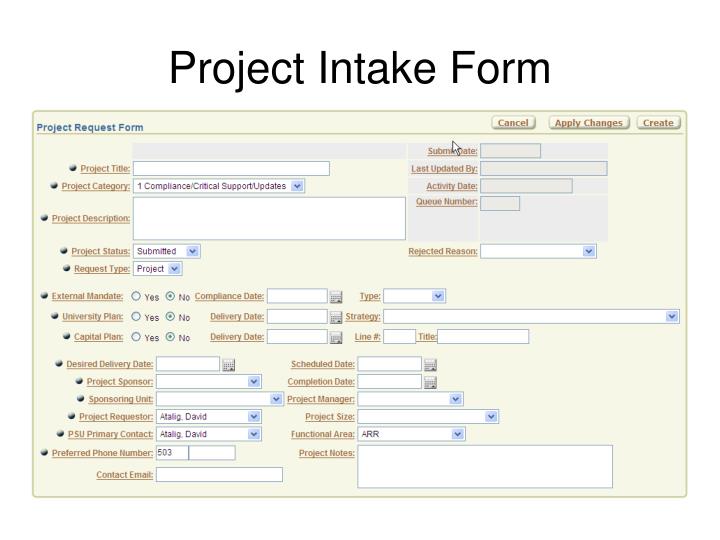
project intake form n, image source: www.slideserve.com
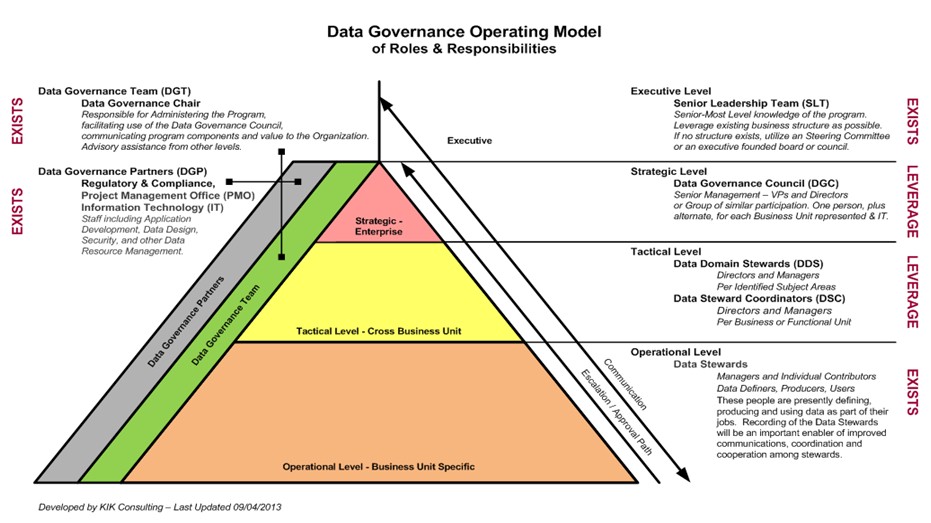
roles, image source: tdan.com
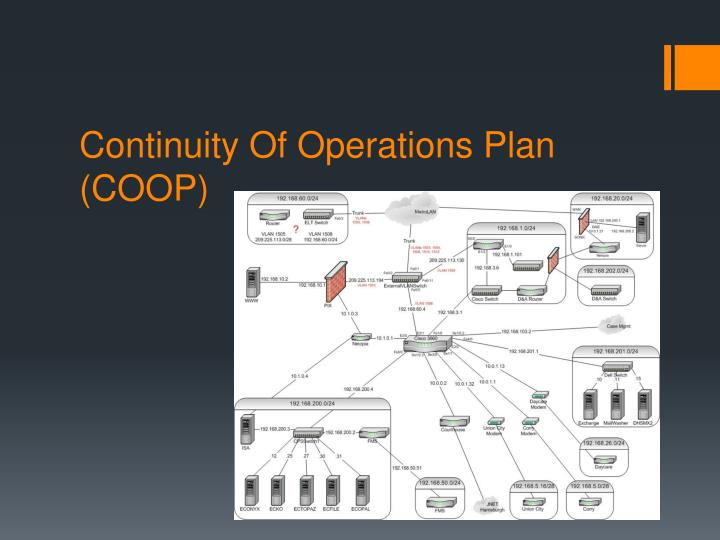
continuity of operations plan coop3 n, image source: www.slideserve.com

en_thankyou_v007, image source: www.mobileye.com

room rentals, image source: tewa.ca

Chinese_Taipei_Olympic_Flag_in_London, image source: en.wikipedia.org

